
In 1999, Scott McNealy, then the CEO of Sun Microsystems, was famously quoted dismissing Internet security as hopeless. “You have zero privacy anyway,” he said. “Get over it.” It was a provocative notion, but let's just say the European Union's regulators don't think that way.
The EU's new cybersecurity rules—the General Data Protection Regulation (GDPR)—will be enforced starting on May 25 of this year. The GDPR applies to any organization that does business in the European Union, not just companies based in EU countries, and organizations that don't meet its requirements could conceivably face fines equal to 20 million euros or 4 percent of their global annual revenue.
Marsh surveyed 1,300 executives globally, and 65 percent said their organization either had plans to comply with the GDPR or were already set. But 11 percent said they had not developed a plan or weren't planning to create one. And 24 percent didn't know.
On its face, the GDPR may look like just another regulatory burden with a complex compliance process. But organizations may be able to turn compliance into a competitive advantage. That's because the GDPR gives treasury teams a strong incentive to improve their cybersecurity practices, which are ever more important in a technologically driven world. Treasurers can use GDPR compliance requirements as a motivator for optimizing the resources they devote to cyber risk management—which, in turn, can enable confident, informed risk-taking that supports business growth.
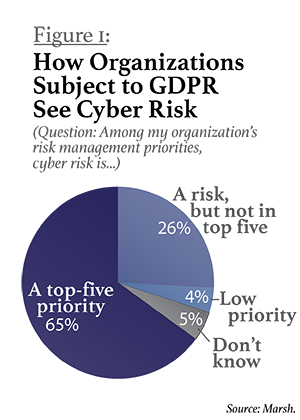
Significantly, among Marsh's survey respondents whose organizations are subject to GDPR, 65 percent said cyber risk is one of their top five risk management priorities (see Figure 1, below). Cyber risks ranked up there with natural disasters, major acts of violence or terrorism, and political upheaval. Their answers show that awareness is up dramatically: In a similar survey Marsh conducted in continental Europe a year before, only 32 percent rated cyber threats as a top-five risk. If nothing else, the approaching GDPR deadline has been a wake-up call for many companies.
 Still, the May deadline may lead to a lot of sleepless nights for corporate executives. Analysts at Oliver Wyman, another operating company of Marsh & McLennan Companies, predict that fines and penalties in the U.K. in the first year alone may total £5 billion, or about US$7 billion, among FTSE 100 companies that fail to comply with GDPR. The totals worldwide could be much higher.
Still, the May deadline may lead to a lot of sleepless nights for corporate executives. Analysts at Oliver Wyman, another operating company of Marsh & McLennan Companies, predict that fines and penalties in the U.K. in the first year alone may total £5 billion, or about US$7 billion, among FTSE 100 companies that fail to comply with GDPR. The totals worldwide could be much higher.
Take a moment to absorb those numbers. Most companies that are unprepared for GDPR will probably not pay the maximum fines, but do they want to take the chance? Of all the risks an organization faces, how many could wipe 4 percent of annual turnover off the books in a heartbeat?
What Is the GDPR?
The General Data Protection Regulation focuses on protecting the personal data of EU residents. It restricts the types of information organizations can collect and use, and requires greater openness about what happens to it, including disclosures if data is lost in a cyberattack. The GDPR defines personal data as “any information related to a natural person or 'data subject' that can be used to directly or indirectly identify the person.” That includes name, email address, computer IP address, bank details, medical information, photo, or information posted on social networking sites. It's difficult to imagine a company that does not store this type of data on at least some of its customers, suppliers, or employees.
Most of the cybersecurity measures that GDPR encourages companies to take are technical; they're the kinds of things an IT department might already be doing to keep up a network's defenses against possible attacks. The problem, of course, is that cyber risk is evolving very quickly. As soon as a company fixes one weakness, attackers will find another.
Here is a better approach: Think of cybersecurity as not just a technical risk—something to try to prevent—but also a business risk, something to be managed intelligently. Cyber risk is not just an IT issue; it ultimately deserves the attention of the C-suite. Think dollars, not bytes.
To that end, companies will benefit if they quantify cyber risk in economic terms. Doing so helps focus staff on building the organization's resiliency in the face of inevitable attacks. This is key. Companies must think in terms of minimizing the business disruption caused by an attack, since defensive measures can do only so much.
Among companies that are planning to comply with GDPR, Marsh's survey found that:
- 56 percent have encrypted organizational desktop and laptop computers,
- 56 percent have conducted penetration testing,
- 56 percent have improved their vulnerability and patch management,
- 67 percent have conducted a cybersecurity gap assessment, and
- 65 percent have implemented or stepped up phishing awareness training for their employees.
As you might expect, there is significant overlap in these numbers. If an organization is sufficiently concerned about cyber risk to take one of these steps, it will generally take others.
The Goal: Resiliency, Not Just Defense
Keeping a business healthy is, of course, what cybersecurity is all about. The stories are now legion of companies that were brought to a halt because a never-seen attacker found a weakness that was years old, or because one employee was fooled by a phishing email or lost a flash drive with sensitive data on it. Companies that take all the best security steps can still be laid low if their vendors or contractors don't also follow their protocols. The cost of such lapses is often fearsome, in terms of business interruption, reputational damage, deals not made, or loss of potential partners that decide to take their business elsewhere.
But while the costs can be fearsome, they are quantifiable. And they become less fearsome when a company puts dollar figures on them. If you can quantify the risks you face, you will have a better sense of where to dedicate your security resources.
Forty-five percent of the executives responding to Marsh's survey said their organization had given an economic estimate to its vulnerability to cyberattack. That's not a majority, and among the companies that made the effort, only 24 percent actually express cyber risks in hard numbers. Most rely on qualitative indicators—the green, yellow, and red of a traffic light, for instance—to signal their level of concern.
Tactics vs. Strategy
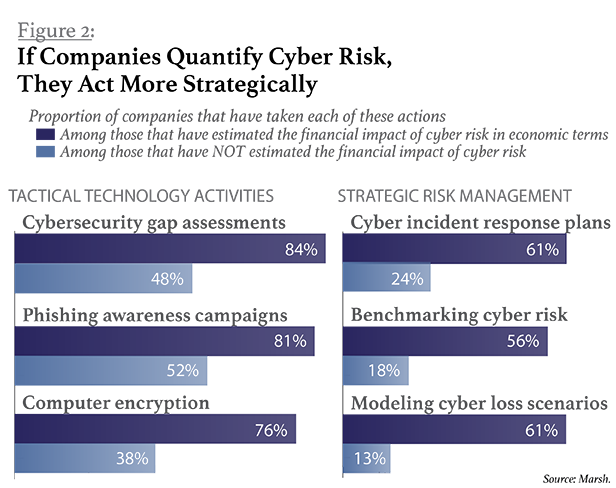
Those that do use numbers are more likely to be strategic in their efforts to manage cyber risks. They think of cybersecurity as a matter of making their corporate defenses more robust, and they take a more comprehensive approach than simply beefing up IT defenses against ever-changing methods of attack. On a practical level, that means these companies have taken such measures as developing a comprehensive plan for responding to cyber incidents, modeling potential loss scenarios, and organizing legal and communications support in case of an attack. Some have also bought insurance against losses incurred in a cyberattack. (See Figure 2, below.)
In contrast, companies that have not quantified their vulnerabilities tend to be more tactical. They may, for instance, warn employees to be wary of unfamiliar emails or conduct tests to see where their online systems need patching. Such steps are useful, but they're not as important in the long term as having an overarching strategy to build resiliency in the organization's response to attack. That's why there is such benefit to assigning actual numbers to cyber risks.
If GDPR can push companies to think more holistically about cyber risk, it will be a good thing. We all know how high the stakes are. In 1975, according to the advisory firm Ocean Tomo, 83 percent of the market value of S&P 500 companies was tied to tangible assets, such as factories and manufactured goods. Today, 84 percent is information-based—ranging from consumer and transactional data to private medical files to proprietary business software.
Mitigation and Transfer
Possible corporate responses to cyber risks fall into four broad categories. First, companies may think their best bet is simply to avoid the risk. Ultimately, though, that is not possible. Every company doing business today faces some degree of cyber threats.
A second approach is to accept the risk. This is certainly part of every organization's response; cyber risks are so prevalent that they cannot be entirely avoided. But that cannot become an excuse to do nothing.
A company's third option is to mitigate the risk. Most companies are already routinely doing this in some way. They employ IT security specialists. They install firewalls and buy antivirus software, and they contract with the vendors for advice.
Finally, a company can consider transferring the risk—in other words, making plans so that when things go wrong, the organization does not assume the entire financial responsibility on its own.
The best corporate cyber risk management plans strike a balance between risk mitigation and risk transfer. Companies protect themselves, but only to the degree that it is cost-effective given their quantification of the risks they face. If a company plans well, it will be able to maintain operations in the face of an attack, recover quickly from any harm, protect its reputation, and remain in compliance with regulatory requirements.
Determining What Actions to Take
So, how can corporate CFOs and risk managers determine how to structure their organization's cybersecurity practices in light of the GDPR? They would do well to ask the following questions:
1. Have we calculated the value of our cyber assets at risk? Quantification can make a significant difference. If a company knows what its worst-case losses could be—expressed in dollars, euros, or another hard number—it is more likely to build strategies to bounce back quickly. As the saying goes, you can't manage what you can't measure.
2. What process do we use internally to identify likely cyber events? And what scenario modeling do we engage in to assess the potential impact of cyberattacks? Gap assessments, tabletop exercises, and similar measures all help. They lead to vulnerability management so that a company can better plan for attacks.
3. What stakeholders are involved in our cyber risk planning? Cyber risk is best managed if it includes an organization's C-suite and board of directors. Risk officers are valuable as coordinators. In Marsh's survey, 70 percent of respondents said their IT departments are the principal “owners” of cyber risk. There is no question that technological defenses are important, but they should not be isolated from the rest of the organization.
4. What risks beyond data breach have we assessed? Depending on an organization's expertise in cyber issues, outside counsel may be helpful. It is important, no matter how hard, to be as imaginative as the unseen attackers, who are constantly hatching new schemes.
The biggest challenge in cyber risk management is for companies to look at the big picture. But the impending GDPR regulations give organizations impetus to do just that. If they approach cyber risk strategically and quantitatively, and if they integrate it into the way they operate, they can become more robust and recover more quickly from attacks.
We cannot eliminate cyber risk, at least not anytime soon. But we can make it manageable.
 Thomas Reagan is the cyber practice leader at Marsh. Based in New York, he oversees client advisory and placement services for cyber risk throughout the country. Reagan recently led development of Marsh's innovative Cyber ECHO and Cyber CAT cyber and privacy insurance products. He also serves as the senior cyber adviser for some of Marsh's largest clients.
Thomas Reagan is the cyber practice leader at Marsh. Based in New York, he oversees client advisory and placement services for cyber risk throughout the country. Reagan recently led development of Marsh's innovative Cyber ECHO and Cyber CAT cyber and privacy insurance products. He also serves as the senior cyber adviser for some of Marsh's largest clients.
© Touchpoint Markets, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more inforrmation visit Asset & Logo Licensing.



